What is HELP_DECRYPT and How to Remove it?
If you are seeing HELP_DECRYPT files on your computer, then it means you are infected with ransomware. The ransomware encrypts all your file and asks ransom for the decryption key. HELP_DECRYPT file contains the instructions about how you can decrypt the files. It tells you that your files are encrypted with RSA-2048 encryption method. It is not possible to decrypt these files unless you pay the ransom. HELP_DECRYPT asks you to pay the ransom with Bitcoin, which is untraceable. There is no guarantee that they will provide the decryption key after paying the ransom. Here in this article, you will know how to remove HELP_DECRYPT ransomware.Reading: what is help decrypt
What is HELP_DECRYPT?
Contents
HELP_DECRYPT is usually a text or HTML file that appears after your PC is infected with Cryptowall 3.0 ransomware. It contains the instructions that what happens to your files. Also, it tells you how you can decrypt your files. It asks you to pay the ransom via Bitcoin. So, the officials cannot catch them because Bitcoin is untraceable. HELP_DECRYPT also lists a deadline on which you need to pay the ransom. Otherwise, they will increase the ransom amount. HELP_DECRYPT is nothing but a ransom note. Ransomware leaves it on your desktop and in the folders so that you can know how to deliver the ransom.To remove HELP_DECRYPT you need to remove the ransomware. Follow the below instructions to remove it.
- 1. What is CryptoWall 3.0?
- 2. How did the CryptoWall 3.0 ransomware get on my computer?
- 3. Is my computer infected with CryptoWall 3.0 ransomware?
- 4. Is it possible to decrypt files encrypted by CryptoWall 3.0 ransomware?
- 5. How to remove the CryptoWall 3.0 ransomware (Virus Removal Guide)
- 6. How to prevent your computer from becoming infected by CryptoWall 3.0 ransomware
1. What is CryptoWall 3.0 ransomware?
- Ransomware family: CryptoWall
- Extensions: .crypto
- Ransom note: HELP_DECRYPT
- Ransom: $500 to $1000
- Contact: None
This CryptoWall 3.0 ransomware variant restricts access to data by encrypting files with the .crypto extension. It then attempts to extort money from victims by asking for “ransom”, in form of Bitcoin cryptocurrency, in exchange for access to data.This ransomware targets all versions of Windows including Windows 7, Windows 8.1 and Windows 10. CryptoWall 3.0 ransomware searches for files with certain file extensions to encrypt. The files it encrypts include important productivity documents and files such as .doc, .docx, .xls, .pdf, among others. When these files are detected, this infection will change the extension to .crypto, so they are no longer able to be opened.The CryptoWall 3.0 ransomware changes the name of each encrypted file to the following format: .crypto.Files targeted are those commonly found on most PCs today; a list of file extensions for targeted files include:.sql, .mp4, .7z, .rar, .m4a, .wma, .avi, .wmv, .csv, .d3dbsp, .zip, .sie, .sum, .ibank, .t13, .t12, .qdf, .gdb, .tax, .pkpass, .bc6, .bc7, .bkp, .qic, .bkf, .sidn, .sidd, .mddata, .itl, .itdb, .icxs, .hvpl, .hplg, .hkdb, .mdbackup, .syncdb, .gho, .cas, .svg, .map, .wmo, .itm, .sb, .fos, .mov, .vdf, .ztmp, .sis, .sid, .ncf, .menu, .layout, .dmp, .blob, .esm, .vcf, .vtf, .dazip, .fpk, .mlx, .kf, .iwd, .vpk, .tor, .psk, .rim, .w3x, .fsh, .ntl, .arch00, .lvl, .snx, .cfr, .ff, .vpp_pc, .lrf, .m2, .mcmeta, .vfs0, .mpqge, .kdb, .db0, .dba, .rofl, .hkx, .bar, .upk, .das, .iwi, .litemod, .asset, .forge, .ltx, .bsa, .apk, .re4, .sav, .lbf, .slm, .bik, .epk, .rgss3a, .pak, .big, wallet, .wotreplay, .xxx, .desc, .py, .m3u, .flv, .js, .css, .rb, .png, .jpeg, .txt, .p7c, .p7b, .p12, .pfx, .pem, .crt, .cer, .der, .x3f, .srw, .pef, .ptx, .r3d, .rw2, .rwl, .raw, .raf, .orf, .nrw, .mrwref, .mef, .erf, .kdc, .dcr, .cr2, .crw, .bay, .sr2, .srf, .arw, .3fr, .dng, .jpe, .jpg, .cdr, .indd, .ai, .eps, .pdf, .pdd, .psd, .dbf, .mdf, .wb2, .rtf, .wpd, .dxg, .xf, .dwg, .pst, .accdb, .mdb, .pptm, .pptx, .ppt, .xlk, .xlsb, .xlsm, .xlsx, .xls, .wps, .docm, .docx, .doc, .odb, .odc, .odm, .odp, .ods, .odtOnce your files are encrypted with the .crypto extension, this ransomware will create the HELP_DECRYPT ransom note in each folder that a file has been encrypted and on the Windows desktop. When the infection has finished scanning your computer it will also delete all of the Shadow Volume Copies that are on the affected computer. It does this so that you cannot use the shadow volume copies to restore your encrypted files.
2. How did the CryptoWall 3.0 ransomware get on my computer?
The CryptoWall 3.0 ransomware is distributed via spam email containing infected attachments or by exploiting vulnerabilities in the operating system and installed software.Cyber-criminals spam out an email, with forged header information, tricking you into believing that it is from a shipping company like DHL or FedEx. The email tells you that they tried to deliver a package to you, but failed for some reason. Sometimes the emails claim to be notifications of a shipment you have made. Either way, you can’t resist being curious as to what the email is referring to – and open the attached file (or click on a link embedded inside the email). And with that, your computer is infected with the CryptoWall 3.0 ransomware.This ransomware was also observed attacking victims by hacking open Remote Desktop Services (RDP) ports. The attackers scan for the systems running RDP (TCP port 3389) and then attempt to brute force the password for the systems.
3. Is my computer infected with CryptoWall 3.0 Ransomware?
When CryptoWall 3.0 ransomware infects your computer it will scan all the drive letters for targeted file types, encrypt them, and then append the .crypto extension to them. Once these files are encrypted, they will no longer able to be opened by your normal programs. When this ransomware has finished encrypting the victim’s files, it will create a HELP_DECRYPT text file which includes instructions on how to recover the files.Below is the message that you will see in the HELP_DECRYPT file:What happened to your files?All of your files were protected by a strong encryption with RSA-2048 using CryptoWall. More information about the encryption keys using RSA-2048 can be found here: topqa.info/wiki/RSA_(crypto system)What does this mean?This means that the structure and data within your files have been irrevocably changed, you will not be able to work with them, read them or see them, it is the same thing as losing them forever, but with our help, you can restore them.How did this happen?Especially for you, on our server was generated the secret key pair RSA-2048 – public and private. All your files were encrypted with the public key, which has been transferred to your computer via the Internet. Decrypting of your files is only possible with the help of the private key and decrypt program, which is on our secret server.What do I do?Alas, if you do not take the necessary measures for the specified time then the conditions for obtaining the private key will be changed. If you really value your data, then we suggest you do not waste valuable time searching for the solutions because they do not exist. For more specific instructions, please visit your personal home page, there are a few different addresses pointing to your page below:Read more: What zodiac sign is may 30th1. hxxps://link 2. hxxps://link 3. hxxps://linkIf for some reasons the addresses are not available, follow these steps:1. Download and install tor-browser: hxxp://www.torproject.org/projects/topqa.info 2. After a successful installation, run the browser and wait for initialization. 3. Type in the address bar: [letters] 4. Follow the instructions on the site.
4. Is it possible to decrypt files encrypted with the CryptoWall 3.0 ransomware?
The security companies and government officials often release decryptors for ransomware. You can take help of these decryptors to decrypt your encrypted files by CryptoWall 3.0 ransomware.However, it is not necessary that decryptors are available for kind and type of the ransomware you got infected. Especially if the ransomware is new and widespread, then it is most likly that you won’t find decryptors for it. If it is an old and popular ransomware then you might find the decryptors. The first step towards finding the decryptor is to know the acutal name and type of ransomware you get infected. To do that you can take help of topqa.info. Visit the website and paste the ransom note in box provided. You can also upload the encrypted file to know the ransomware name. Once you do that click on GO! FIND OUT button.Now the website will tell you about the type of ransomware and also provide you link if there is a decryptor available.ID Ransomware is a similar website, you can upload the ransom note, sample encrypted file, or the contact email address to know about the type of ransomware. Once you know about it you can find the decryptors on the internet. But do not download decryptors from shady websites they may further infect your computer.If you haven’t find the decryptors then it is not possible to get your files back. That doesn’t mean you should pay ransom to the cybercriminals. Do not pay any money to recover your files. Even if you were to pay the ransom, there is no guarantee that you will regain access to your files.If you’ve already paid the ransom, immediately contact your bank and your local authorities. If you paid with a credit card, your bank may be able to block the transaction and return your money. You can also contact the following government fraud and scam reporting websites:
- In the United States, go to the On Guard Online website.
- In Australia, go to the SCAMwatch website.
- In Canada, go to the Canadian Anti-Fraud Centre.
- In France, go to the Agence nationale de la sécurité des systèmes d’information
- In Germany, go to the Bundesamt für Sicherheit in der Informationstechnik website.
- In Ireland, go to the An Garda Síochána website.
- In New Zealand, go to the Consumer Affairs Scams website.
- In the United Kingdom, go to the Action Fraud website.
If your country or region isn’t listed here, we recommend that you contact your country or region’s federal police or communications authority.
5. How to remove the CryptoWall 3.0 ransomware (Virus Removal Guide)
STEP 1: Use MalwareFox to remove CryptoWall 3.0 ransomware
MalwareFox is antimalware that works on heuristic approach to detect and remove malware from your PC. It analyzes the malware signatures as well as their behaviour. If a program acts like a malware then MalwareFox blocks it right there. It is lightweight on your system resource and finishes the scan quickly.Its not like I am recommending you to install a costly software to remove the malware. The MalwareFox subscription charges are fairly low. But that is for a fully featured program with real-time protection capabilities. The scanning works even with the free version, though you can try the MalwareFox Premium for 14 days. Also, you don’t need to remove your current antivirus, MalwareFox will work effectively without any conflicts.
 You will see an User Account Control pop-up asking if you want to allow MalwareFox to make changes to your device. Click on “Yes” to proceed with the installation steps.
You will see an User Account Control pop-up asking if you want to allow MalwareFox to make changes to your device. Click on “Yes” to proceed with the installation steps. 
 Then the MalwareFox installation Wizard appears, click on Next and follow the screen instructions to setup MalwareFox on your PC.
Then the MalwareFox installation Wizard appears, click on Next and follow the screen instructions to setup MalwareFox on your PC.  Once the installation is complete, MalwareFox will download the latest version and virus signatures from the server. Let it update.
Once the installation is complete, MalwareFox will download the latest version and virus signatures from the server. Let it update. 

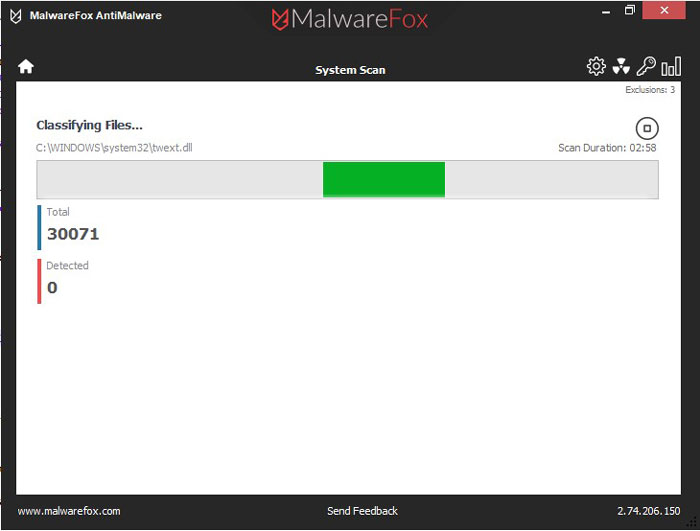
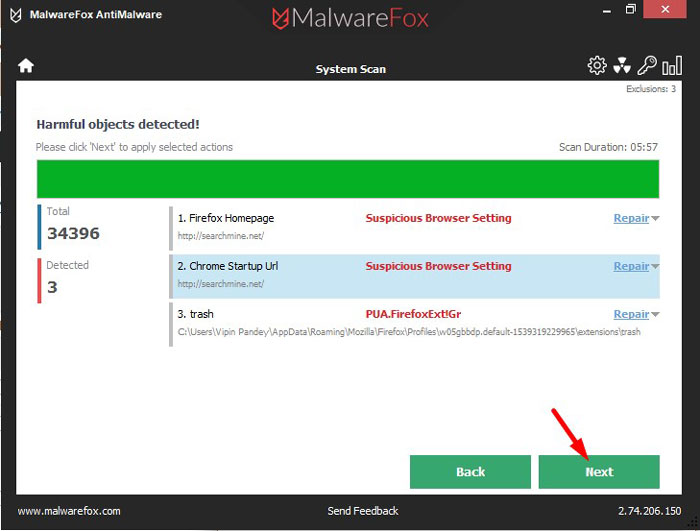 When the malware removal process is complete, you can close MalwareFox and continue with the rest of the instructions.
When the malware removal process is complete, you can close MalwareFox and continue with the rest of the instructions.STEP 2: Use HitmanPro to scan for malware and unwanted programs
HitanPro works on unique cloud-based approach to detect the threats. You can use it as a second opinion malware scanner. HitmanPro also observe the behaviour active programs and checks the locations where malware normally resides. If there is a suspicious file then it upload thes file to cloud where it is scanned by Bitdefender and Kaspersky antivirus engines.HitmanPro is available for a 30-days trail that lets you to clean the threats. After that you may need to purchase it which costs around $24.95 for 1 year single PC. If you won’t upgrade then you can scan using the HitmanPro however it won’t let you remove or quarntine the detected threat.
 Now you will see an User Account Control pop-up asking if you want to allow HitmanPro to make changes to your device. Click “Yes” to install it on your PC.
Now you will see an User Account Control pop-up asking if you want to allow HitmanPro to make changes to your device. Click “Yes” to install it on your PC. 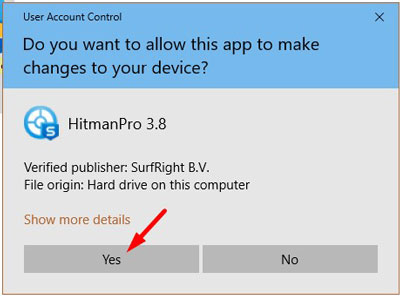
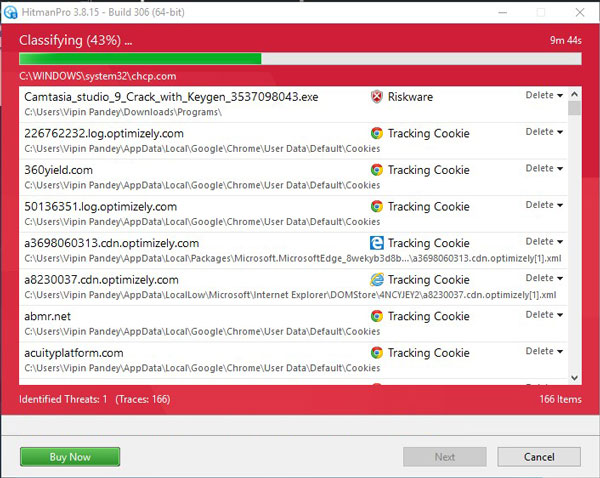
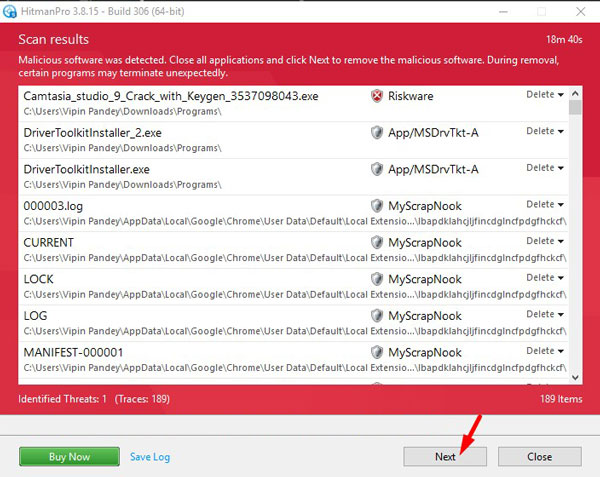 When the process is complete, you can close HitmanPro and continue with the rest of the instructions.
When the process is complete, you can close HitmanPro and continue with the rest of the instructions.STEP 3: Restore the files encrypted by CryptoWall 3.0 ransomware with recovery software
Option 1: Restore your files encrypted by CryptoWall 3.0 ransomware with ShadowExplorerCryptoWall 3.0 will attempt to delete all shadow copies when you first start any executable on your computer after becoming infected. Thankfully, the infection is not always able to remove the shadow copies, so you should continue to try restoring your files using this method.
Option 2: Restore your files encrypted with the CryptoWall 3.0 extension with File Recovery SoftwareWhen the files are encrypted with the CryptoWall 3.0, this ransomware first makes a copy of them, encrypts the copy, and then deletes the original. Due to this you can use file recovery software such as:
- Recuva You can follow the below guide on how to use Recuva:
How to prevent your computer from becoming infected by CryptoWall 3.0 ransomware
To protect your computer from the CryptoWall 3.0 ransomware, you should a strong antimalware on your system like MalwareFox and keeps its real-time protection enabled. Also, you need to take backup of your personal documents.Your computer should now be free of the CryptoWall 3.0 ransomware infection. If you are still experiencing problems while trying to remove CryptoWall 3.0 ransomware from your computer, please comment below we will try to help you as much as possible.Read more: Sin 30 degrees | Top Q&A
Last, Wallx.net sent you details about the topic “What is HELP_DECRYPT and How to Remove it?❤️️”.Hope with useful information that the article “What is HELP_DECRYPT and How to Remove it?” It will help readers to be more interested in “What is HELP_DECRYPT and How to Remove it? [ ❤️️❤️️ ]”.
Posts “What is HELP_DECRYPT and How to Remove it?” posted by on 2021-09-08 05:36:56. Thank you for reading the article at wallx.net

